Cloud Security
Our Cloud Security service protects your data, applications, and infrastructure across AWS, Azure, and GCP from threats, vulnerabilities, hacking attempts, and misconfigurations. We build a strong, multi-layered security posture aligned with industry best practices, compliance requirements, and the cloud shared-responsibility model—ensuring your environment stays secure, resilient, and ready for evolving risks.
Key Outcomes
Reduced Risk & Strong Compliance
Maintain continuous alignment with global security standards such as ISO 27001, GDPR, HIPAA, and PCI DSS while significantly lowering your cloud attack surface.
Proactive Threat Detection
Leverage real-time monitoring, advanced analytics, and automated response workflows to identify and contain threats before they disrupt operations.
Secure by Design
Embed security at every stage of the development lifecycle—applying DevSecOps practices, automated checks, and policy enforcement to stop vulnerabilities from reaching production.
Enhanced Security Assurance
Strengthen your environment through threat modeling, regular penetration testing, and architectural reviews that uncover weaknesses early and guide remediation.
Service Focus Areas
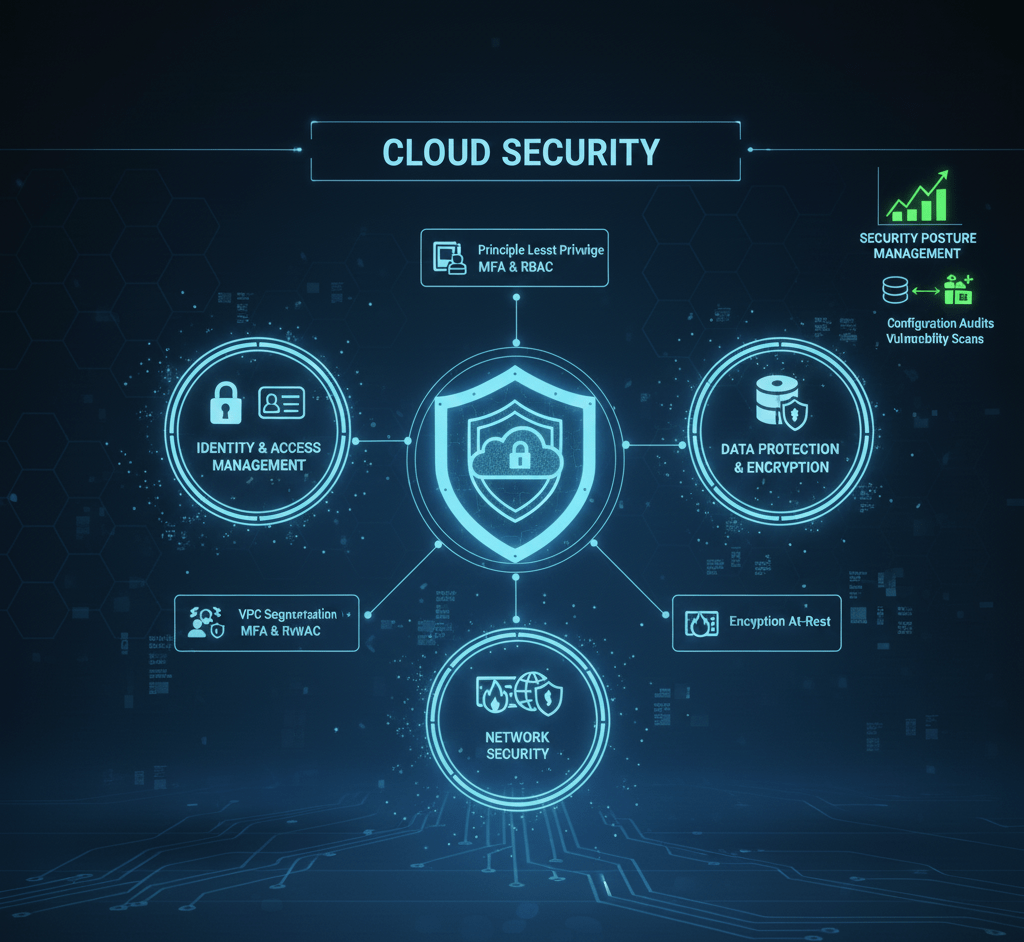
Identity & Access Management (IAM)
Design and enforce principle-of-least-privilege access, strong MFA policies, and robust RBAC structures to ensure users and workloads operate with only the permissions they truly need.
Network Security
Segment networks strategically using VPCs/VNets, subnets, and security groups. Configure cloud-native firewalls, WAFs, and intelligent traffic filtering to defend against malicious access and common exploits.
Data Protection & Encryption
Classify sensitive data, enforce encryption using native KMS services, and implement secure, immutable, versioned backups to safeguard data integrity and confidentiality.
Security Posture Management (CSPM)
Continuously scan for misconfigurations, compliance drift, and vulnerabilities across compute, storage, networking, and identities—using cloud-native and third-party tools for centralized visibility.
Threat Modeling & Penetration Testing
Conduct structured threat modeling to anticipate attack vectors and simulate real-world attacks through periodic pentests to validate controls and strengthen defenses.
Compliance Alignment (ISO, GDPR, etc.)
Implement frameworks, controls, and documentation practices needed to meet and maintain ISO 27001, GDPR, and other regulatory obligations.
